

Last updated on
April 25, 2024
Email marketing is a great tool to engage with your customers. You can use it to promote your business through newsletters, discount offers, or product information.
However, emails have also long been the target of cybercriminals who use them to distribute spam, malware, and scams.
As per Greathorn 2021 Email Security Benchmark report, email security was ranked as the top IT security project of 2021.
Therefore, you need to take significant measures to secure your marketing emails. Use two multi-factor authentications (2FA) and a password manager for your accounts. You can also provide limited access to employees for email accounts and educate them about the importance of staying safe online.
Well, in this guide, you will learn how to keep your email marketing safe for your company and customers.
But, let’s first understand email security, its importance, and the common email marketing threats.
Email security refers to the methods and procedures to protect email accounts, content, and communication against unauthorized access, data loss, or other malicious threats.
The techniques and methods include login security, email encryption, spam filtering, fraud prevention, and cybersecurity education.

Email is a play tool for hackers and cybercriminals to spread malware, spam, and phishing attacks. It is also one of the main entry points to access an enterprise network and breach valuable company data.
Around 92% of all malware is delivered through email. 15 Billion spam emails are sent daily, and around 45% of all email is spam.
In addition, 95% of business email compromise losses were between $250 and $984,855.
Therefore, implementing effective security practices is very important.

Here are the six common threats:

Here are the ways that you can teach your employees to spot email threats:
Check for any emails that use display name spoofing to disguise the real sender. These emails look like legitimate entities, or trusted individuals have sent them. Check the header to view the sender’s email address and look for subtle differences, such as extra characters or additional letters.
In addition to checking the header of an email, you also need to check the body of the email. If you notice any strange request that puts you under pressure to take action, then the chances are that it contains malware. Therefore, analyze the language of the email to notice any sense of urgency. Also, check for grammatical errors and spelling mistakes as most spam emails are not well written.
Any email that asks you to verify, review, check, or confirm any information is likely an email containing malware. Therefore, verify the sender's email address before you confirm the information.
An email with an unexpected attachment, asking you to open it can contain malware. Attachment file extensions that can be suspicious are .zip, .xls, .js, .pdf, .ace, .arj, .wsh, .scr, .exe, .com, .bat., and .doc.
Be aware of emails that encourage you to click towards a website. It may have malware! Before clicking on the link, check the URL. If it is a hyperlinked link, then over the text and check the link before you click.
Despite the emergence of team communication tools, such as Slack or MS Teams, emails still are the primary option for many businesses for internal communication.
By 2025, the total number of email users worldwide will be around 4.6 billion.
Therefore, businesses must implement security measures for their email marketing to prevent the risk of email vulnerabilities.
Here are the best actionable steps you can take to protect your company and customers during your email marketing efforts:
Sometimes emails contain customer-sensitive information, making them vulnerable. Therefore, it is crucial to secure these emails by encrypting all emails between you and your customers.

First, you should use an ISP (Internet Service Provider) with a strong reputation for its security. There are cheaper options as well. But a data breach can be even more costly to recover from if the ISP security is weak.
Here are three more ways to encrypt your marketing emails:
In addition, use high-quality email and security tools that are not prone to easy manipulation or infiltration.
Invest in password managing software, phishing, and spoofing blocking software.
Here are a few options:
Moreover, email firewalls allow you to filter emails with attached malware and other problematic materials. Antivirus software can also be used to scan for viruses, worms, and Trojan horses before you download anything.
Other cybersecurity tools that you can use are:
It’s one of the standard practices and an effective security measure. 2FA requires that a user provides two pieces of identifiable information before signing in, making it significantly harder for hackers to get into an account, even if they have the password.
2-Factor Authentication is both free and easy to use. All you need is to tinker with your account settings a little in password management.
Since websites and services do not activate it by default, you have to manually configure it on your account settings. Take a look Gmail’s authentication popup below.
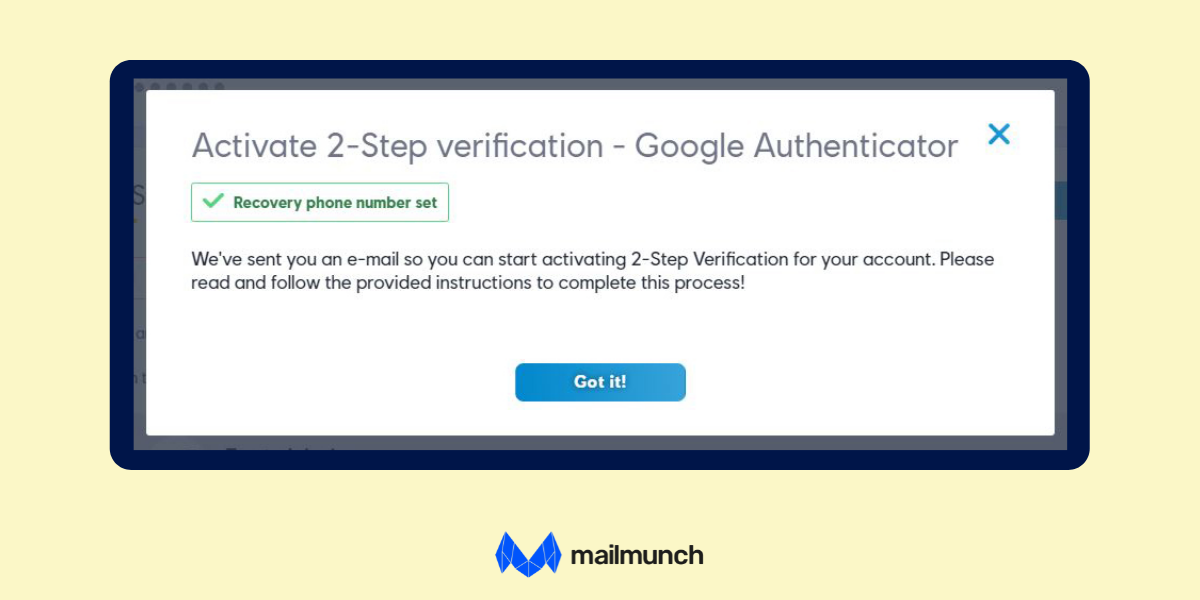
With the emergence of remote work, many employees are encouraged to use their device for working and use it to log in to business email accounts. However, it's way more difficult for an organization to track personal devices, which is a significant security risk.
Employees may have malware on their devices, potentially exposing their login credentials, causing their data to be leaked and further damaged.
If you're an employee, constantly update the device you're using to log in and run antivirus scans to ensure the device isn't infected with malware.
Updating software offers plenty of benefits. Most of the updates include repairing security holes discovered during the update. Plus, it will fix or remove computer bugs.
Other than that, updates can add new features to the device and remove outdated ones. Updating devices regularly is a highly suggested practice.
If your company doesn't use a wireless connection, or if you're working remotely, ensure that you're always connected to the internet via a trusted Wi-Fi network that is adequately protected with WPA.
Public Wi-Fi networks are the most conventional place for hackers to attack.
Suppose you log in to your email while connected to an unknown or publicly accessible network. In that case, anyone could potentially track your actions and gain access to personal information. To avoid this risk, use a well tested VPN.
Trusted Wi-Fi Networks allow transparent data transfer. A computer that uses a trusted network has an Administrator to administer to prevent private and secured data from leaking. Since this network provides limited access and has strong firewalls, the computers are more secure and confidential.
You need to focus on email authentication standards using transactional emails or curated content emails to enhance email security.

These standards give you control over how your domain is used and who is trying to attack your domain. Thus, email authentication standards secure you from becoming victims of spam, spoofing, and phishing attacks.
Here are three email authentication standards:
Email scams are prevalent, and even the most innocent-looking email can contain an attachment causing damage to your computer and email account. Therefore, it is important to learn about email blacklists.
Only open attachments and links from users you trust and investigate the message to ensure it's coming from a reputable source. You can do this by inserting the subject line into a search engine and seeing if other users have received a similar email and reported it as potentially dangerous.
At times attackers send spear-phishing emails that look like they have been sent actually from your friend or your bank. The worst part is that the attackers have taken over a real email account or phone number for phishing purposes.
However, there is a way to combat the situation. If the source is legit, check the texts. The email account with text out of character is the major reason you must doubt its authenticity. Also, if you find anything weird about a message from someone you know, such as if it has a request in it, there is a real possibility that the email is impersonated or the email ID is hacked.
You can activate DMARC domain protections to protect your company from cybercriminals. It helps you to prevent attackers from using a legitimate corporate domain in phishing campaigns.

DMARC uses two email authentication methods:
DMARC email security makes phishing attacks visible, allowing you to gain full insight into your email channels. It also protects your business against spoofing and brand abuse.
However, to achieve high security, you must use DMARC, SPF, and DKIM in combination.
It is important to keep your data safe and confidential, for which you need to have a checklist that you must run regularly to prevent breaches.
Here are some measures that you can take:
An email gateway allows you to scan and process all the emails you sent or receive, ensuring that threats are allowed in. It uses a multi-layered approach to authenticating all the email traffic.
You can implement a secure email gateway on your premises using an appliance, a virtual appliance or a cloud. It depends on the type of email server that you are using. It can be a cloud-based email server, such as Microsoft Office 365 or an on-premises email server, such as Exchange.
While selecting a secure email gateway, you need to consider:
In addition, it is better to create a backup of important and confidential files beforehand as it minimizes the potential damage and devastation in case your systems and network have been attacked.
However, the ransomware variants may sit idle for weeks in some cases. Once triggered, they can destroy backups as well.
Therefore, create additional copies of your critical files in multiple locations and perform restoration exercises regularly. You could also use a backup tool for this purpose. There are many free and paid tools available for this purpose, such as Microsoft Office 365 Backup tool by Nakivo. It backups your office 365 files in case there is an attack.
Educate your customers about email scams through your blogs or FAQs.
Here are the steps you can take to make your customers understand the importance of email cyber crimes:
You need to teach and show your customers what real spam looks like. Emphasize the importance of checking who they are getting a message from. Also, warn the user not to click on any link or attachment from unknown sources.
Email marketing remains the top tool to reach out to new customers. Still, it's essential to stay safe while using it to prevent causing any damage to your customers or organization. This can be done by:
To ensure your email campaigns are encrypted and do not redirect to other sources, use email marketing software like Mailmunch to target your audience, segment the email list, and reach them on time of promotions!
A bookworm and a pet nerd at heart, Summra works as Content Writer at Mailmunch. She loves to play with keywords, titles, and multiple niches for B2B and B2C markets. With her 3 years of experience in creative writing and content strategy, she fancies creating compelling stories that your customers will love, igniting results for your business.
Tags:

M. Usama
April 19, 2024

M. Usama
April 19, 2024

M. Usama
April 18, 2024